What Is Cyber Deception?
Cyber deception manipulates an attacker’s perception by using false information, decoys, and traps to create a misleading impression of the actual state of the network or system.
Optical illusions and cyber deception share several similarities in the way they manipulate perception and the understanding of information. Although used in different contexts — visual and cyber — both rely on tricks to create a false or distorted sense of reality.
Cyber deception technology refers to the use of various methods, tools, and tactics to mislead attackers and redirect their efforts away from real assets. These technologies simulate real systems, data, or applications to lure attackers and analyze their techniques, motives, and behavior.
If we compare it to everyday life, cyber deception is like setting a fake trap for thieves. Imagine having a valuable safe in your home and wanting to protect it from burglars. Instead of simply locking the doors, you place a fake safe that looks real but contains nothing valuable. Intruders, attracted by the fake safe, will attempt to break into it while the real one remains secure and untouched.
As a technique for protecting information systems, cyber deception evolved from early concepts of security and defense. The idea of fake targets and decoys is not new — such tactics have been used in military strategies for centuries before being applied to the digital world. In military conflicts, fake targets and decoys (e.g., false camps or weapons) were used to mislead the enemy. These tactics inspired the development of similar methods in cybersecurity.
In the early days of cybersecurity, the focus was on protecting against external threats using firewalls and antivirus software. However, as attacks became more sophisticated, it became clear that proactive approaches were needed.
How Cyber Deception Works
At its core, the functionality of cyber deception systems can be divided into five key components or activities that require careful attention:
1. Deploying fake assets (honeypots and honeynets)
Honeypots are isolated systems or applications designed to look like legitimate parts of the network. They attract attackers into targeting them, believing they have found a real asset.
Honeynets are networks containing multiple honeypots. They simulate an entire network infrastructure, including various devices and applications, giving attackers the impression that they are targeting a real environment.
2. Luring attackers
The purpose of decoys is to attract attackers with seemingly valuable data and easy access. For example, fake servers may contain what appear to be sensitive financial data or access credentials.
3. Monitoring attacker activity
As attackers interact with fake assets, all their actions are recorded. This includes access attempts, attack methods, installed malware, and other behavior. Modern cyber deception systems use automated tools to track and log attacker activity. These tools can generate detailed reports and real-time alerts, providing full visibility into the infrastructure.
4. Data analysis
The collected data is analyzed to understand attacker techniques, tactics, and procedures. This analysis enables security teams to identify behavioral patterns and new emerging threats. Insights from decoys can be used to enrich threat intelligence, helping organizations strengthen their defenses and minimize the actual attack surface.
5. Improving security measures
Based on attacker activity analysis, organizations can adjust and enhance their security strategies. This may include updating firewalls, access control rules, and improving tools for threat detection and response.
Benefits of Cyber Deception Systems
Cyber deception is a key component of modern cybersecurity strategies. It offers numerous advantages that improve the protection of systems and data. Some of the key benefits include:
- Early threat detection
Cyber deception systems allow for the quick detection of attackers as soon as they attempt to access decoys. This early warning enables rapid response and minimizes damage. - Detailed attack analysis
Decoys collect information about attackers, including their methods, tools, and tactics. This analysis helps security experts understand attackers and develop stronger defensive strategies. - Deterrence
Awareness that an organization uses deception technologies can discourage attackers, as it increases the risk of detection and reduces the likelihood of a successful attack. - Reducing the risk of real damage
By diverting attackers to fake assets, organizations reduce the risk of compromising real systems and data, helping preserve the integrity and security of legitimate resources. - Proactive defense
Cyber deception systems enable organizations to adopt a proactive rather than reactive security approach, significantly improving overall resilience to threats. - Education and training
Beyond these five points, an important additional benefit is user education and training. The collected insights are extremely valuable and can be used to train employees and develop new security policies and procedures.
Strategies for Implementing Cyber Deception Technology
Implementing cyber deception requires careful planning and strategic placement of decoys within the network. The goal is to attract attackers without disrupting production systems, gather useful intelligence, and improve security measures.
Before deploying deception decoys, it is important to conduct a thorough analysis of the network infrastructure and identify key areas that may be targeted. This may include critical applications, servers with sensitive data, or high-risk network segments.
Where to Implement Cyber Deception Technology?
Key points in the network:
DMZ (Demilitarized Zone)
Placing decoys in the DMZ helps protect critical infrastructure and can assist in identifying external threats.
Internal network
Since statistics show that many incidents originate from within the internal LAN, deploying decoys in the internal network helps detect threats that bypass external defenses or originate from insiders.
Designing Decoys
Authenticity
Decoys must look authentic to attract attackers. This means mimicking real data, legitimate system configurations, and plausible activity. This includes simulating operating systems, open ports, applications, and files that could entice attackers.
Diversity
Because attackers use varied techniques and target different parts of critical infrastructure, it is important to deploy a variety of decoys (e.g., web servers, databases, applications) to attract different types of attackers.
Solution Design and Practice
As an example of integrating cyber deception, we will use a solution from Fortinet.
FortiDeceptor is a security product developed by Fortinet, a company specializing in cybersecurity. It is designed to serve as part of a deception technology strategy, aimed at identifying, isolating, and responding to network threats through fake data and resources that appear to be legitimate parts of the IT infrastructure but actually serve to detect and gather intelligence on attackers.
The core functionality of FortiDeceptor is based on creating a network of Decoy VMs to lure attackers and monitor their activity. When attackers target the Decoy VMs, their actions are analyzed to protect the network.
In our example, we will follow an implementation model at one of the critical network points — the DMZ — using a Windows instance.
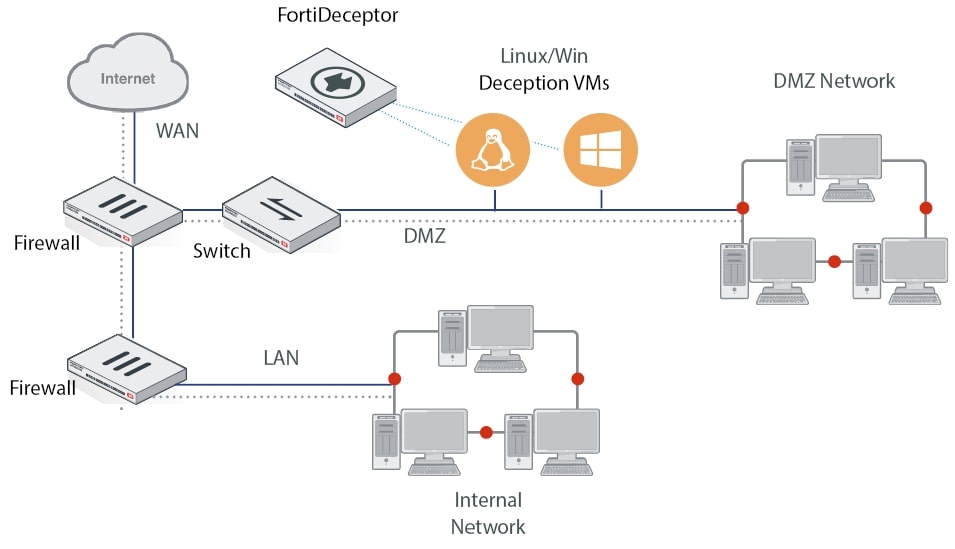
Basic Device Configuration
The basic device configuration can be broken down into several key steps. These primarily include actions such as network preparation, device installation, and connecting to its interface using the configured IP address and default administrative credentials.
Interface
Upon logging into the device, we arrive at the device’s main interface. The FortiDeceptor interface provides users with an intuitive way to configure, manage, and monitor decoys. Some of the main components and functionalities of the FortiDeceptor interface include:
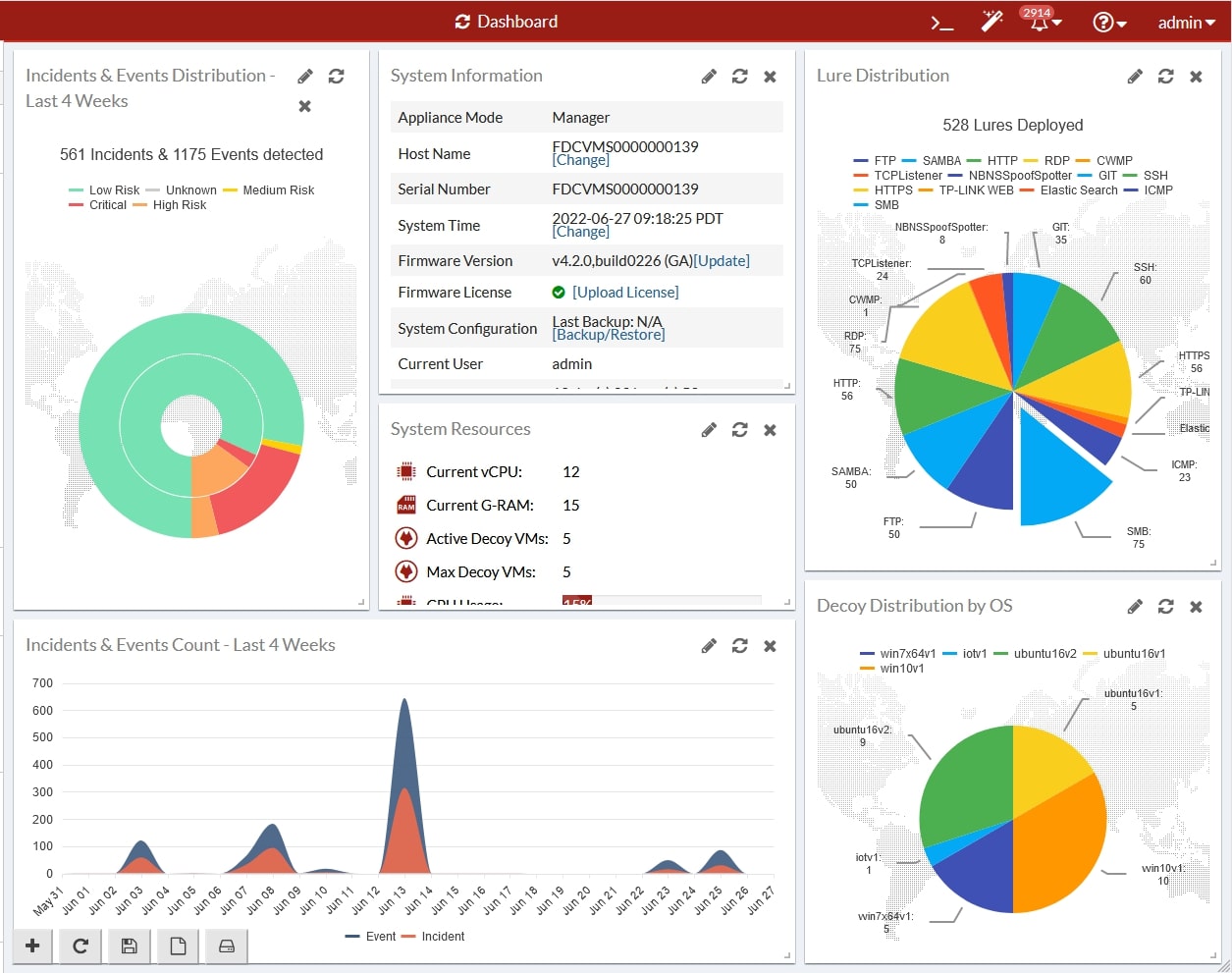
1. Dashboard
The dashboard provides a comprehensive overview of activities:
- Detected threats and attacks
- Status of decoys
- Graphical representation of attacks and penetration attempts
- Options for filtering and customizing the view according to user needs
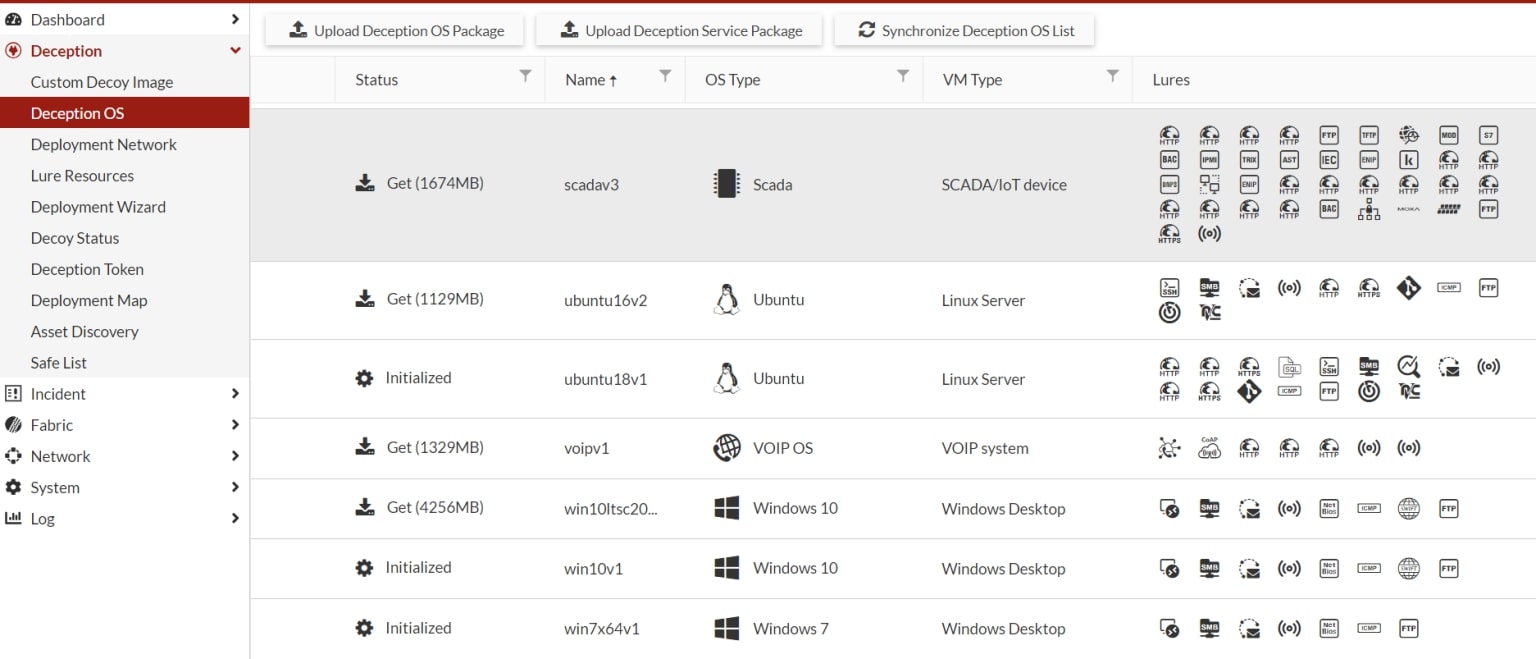
2. Deception (Decoys)
The section for creating, configuring, and managing decoys.
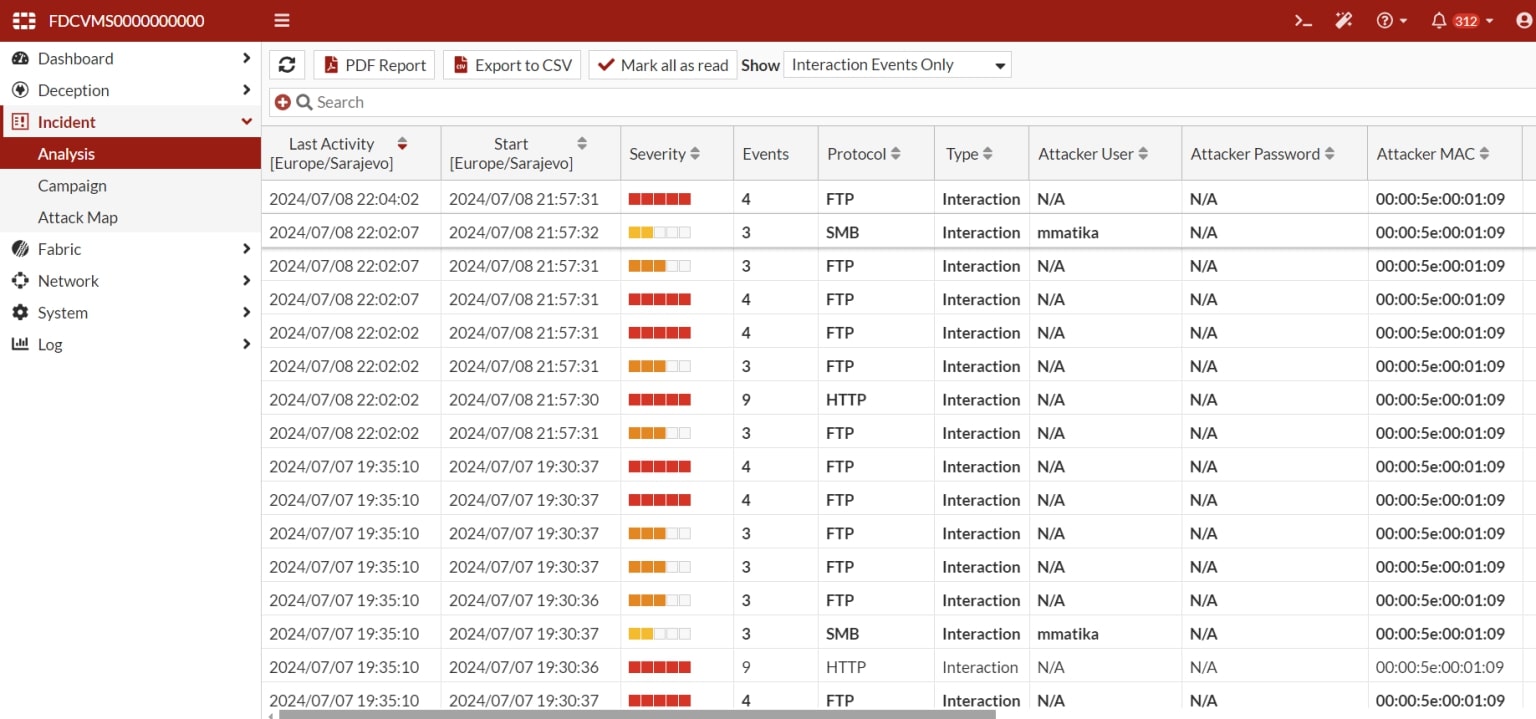
3. Incident
The “Incident” section in FortiDeceptor is essential for monitoring, analyzing, and responding to security events.
Incident Overview:
The incident list displays all incidents detected by FortiDeceptor. Each incident typically includes key information such as the date and time, type of incident, source IP address, and the targeted decoy.
Filters and Search: The ability to filter incidents based on various criteria (date, severity, incident type, IP address, etc.) and search for specific events.
Incident Details:
A summary of the incident provides essential information, including the type of attack, detection time, and affected decoys.
Detailed View: A deeper insight into the incident with extensive information about the attacker, attack methods, tools used, and all relevant data.
Graphical Representation:
A visual representation of the attack flow that helps in better understanding the incident.
Decoy Configuration
The first step in configuring a decoy is selecting the operating system from the repository. In our case, we chose to simulate an Ubuntu operating system with a fake file server role.
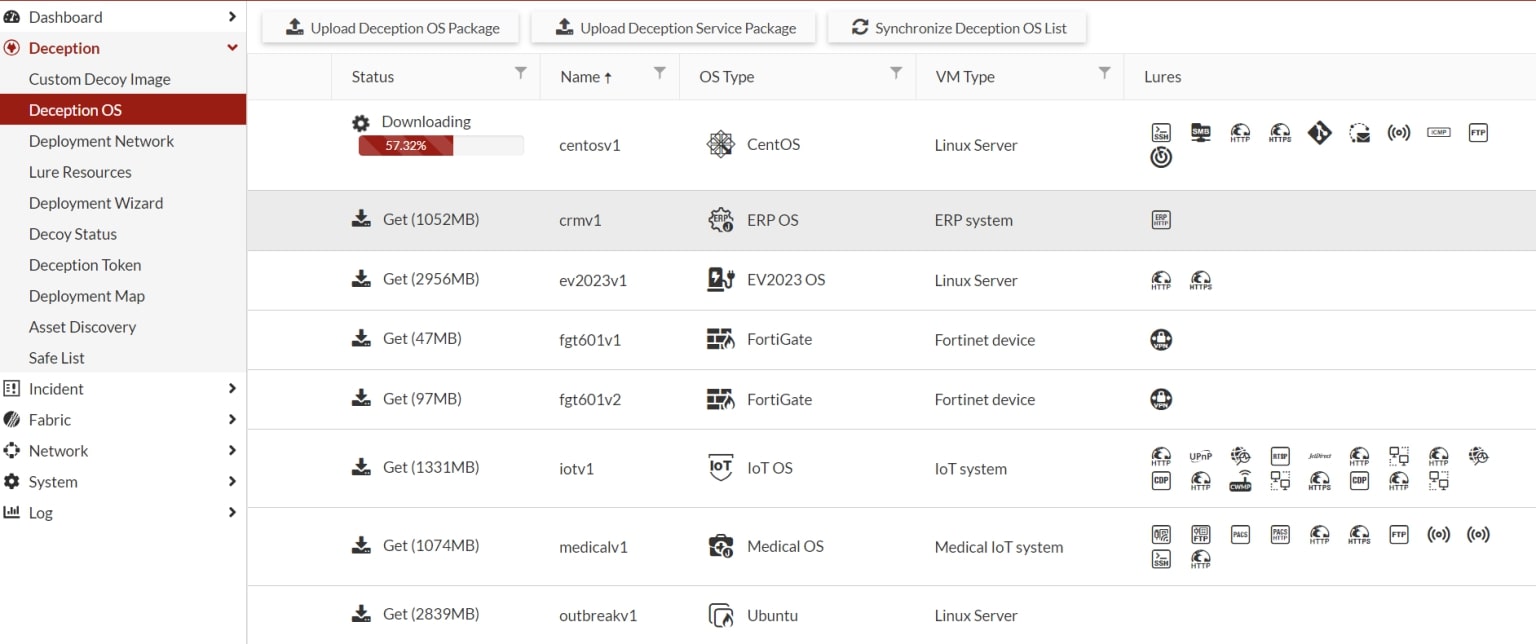
Screenshot 4: Operating system repository view
In the next few steps, through the intuitive interface, we begin the process of initializing a dedicated decoy.
The first step is configuring the network and the network segment where the decoy will be placed.

Screenshot 5: Network settings configuration view
After configuring the network, we proceed to the intuitive process of configuring the cyber deception system.
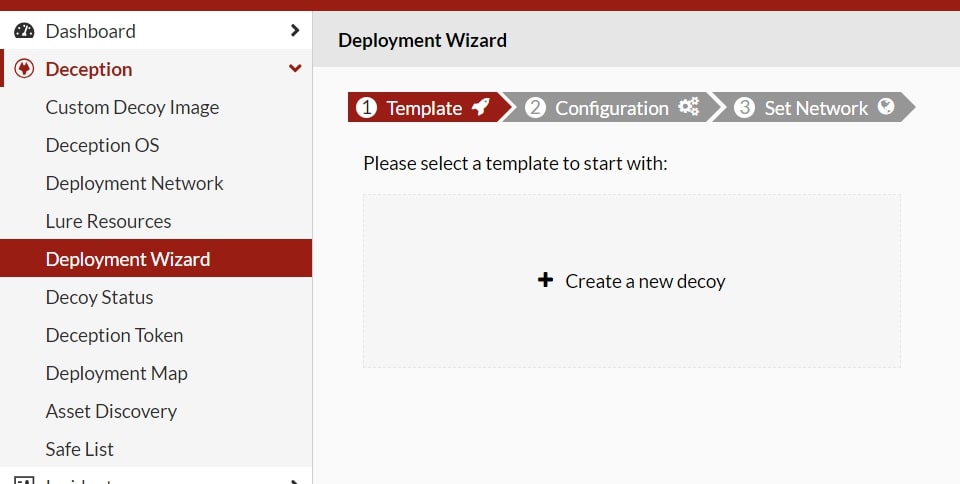
Screenshot 6: Process initialization
The configuration consists of assigning a name to the decoy, selecting the corresponding operating system, and configuring predefined protocol settings.

Screenshot 7: Decoy configuration view
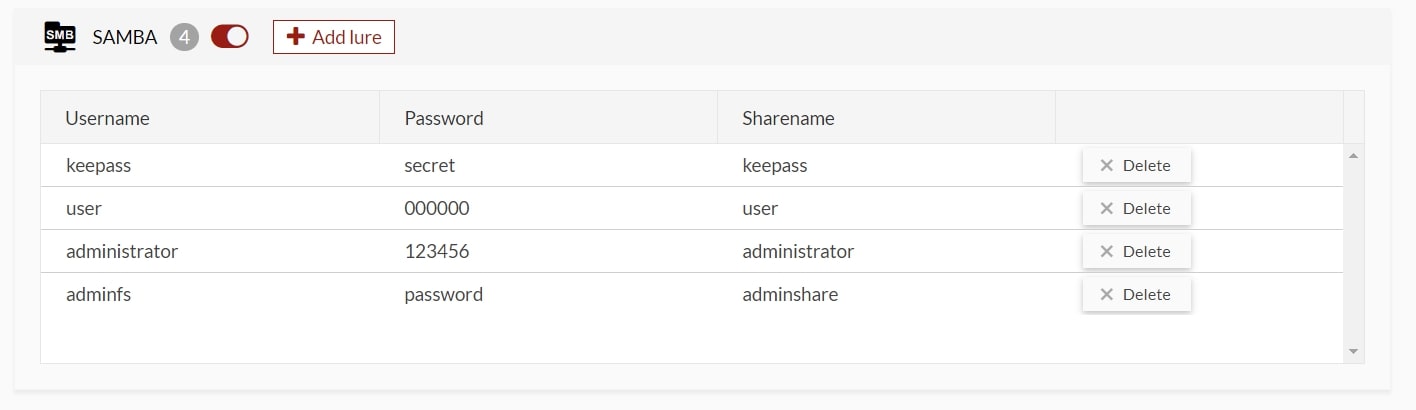
Screenshot 8: View of additional decoy protocol settings
The final step before deployment is defining the network segment, i.e., assigning the network range that was configured in the first step of the setup.
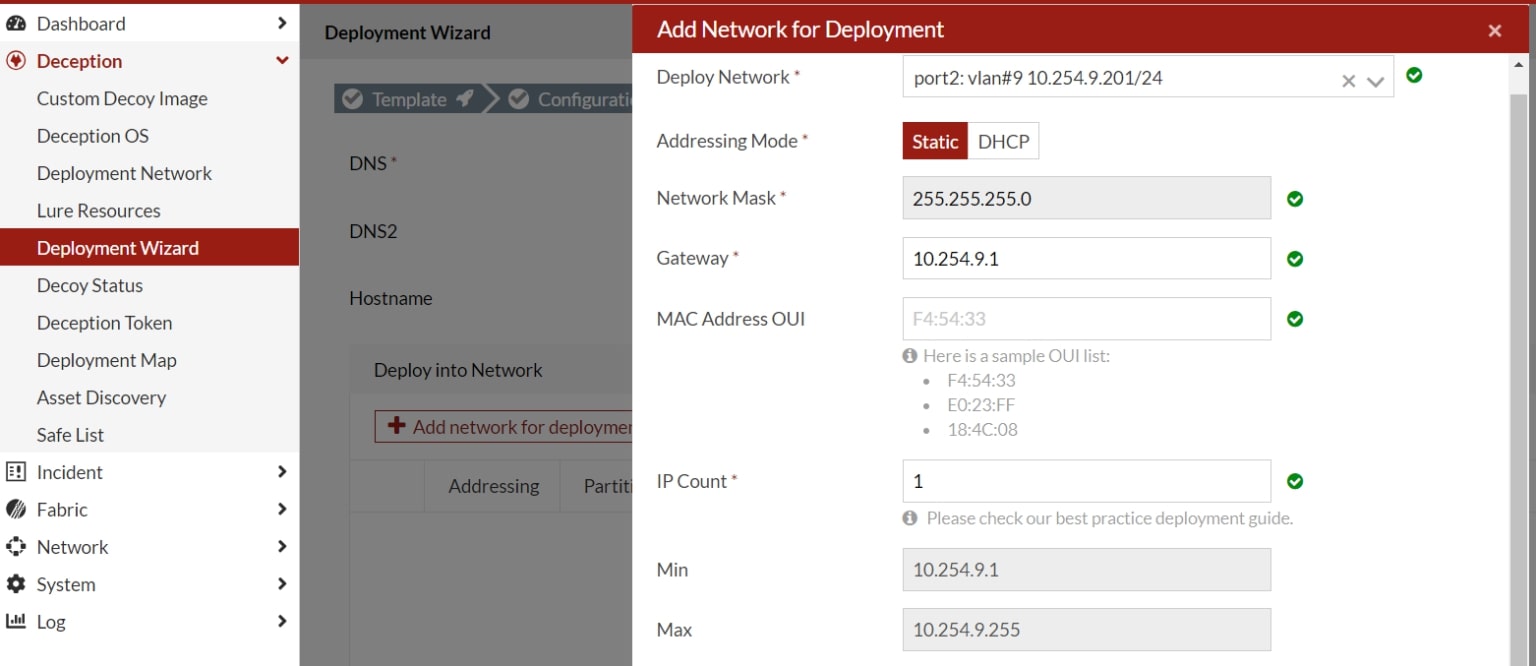
Screenshot 9: Assigning the defined network range
The status of the decoy and its operational state can be checked in the dedicated menu.
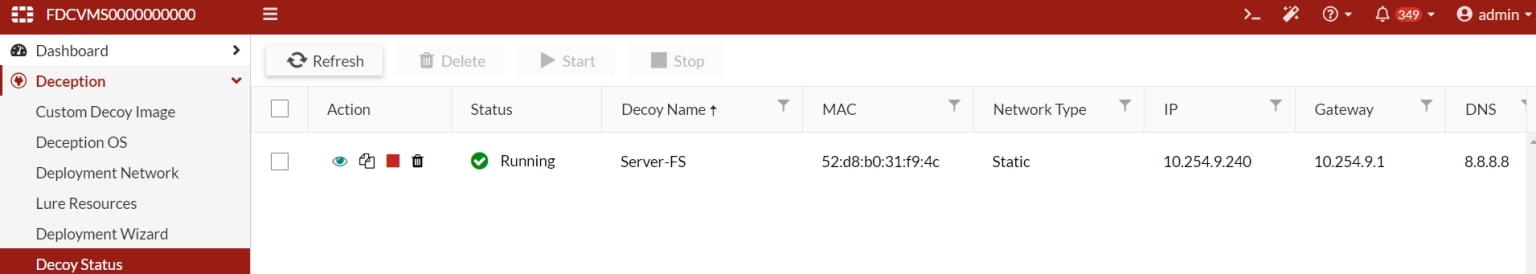
Screenshot 10: Decoy status view
Incident Overview and Analysis
The incident section in FortiDeceptor is crucial for analyzing and responding to security threats detected through decoys. Here is how you can use this section to manage incidents.
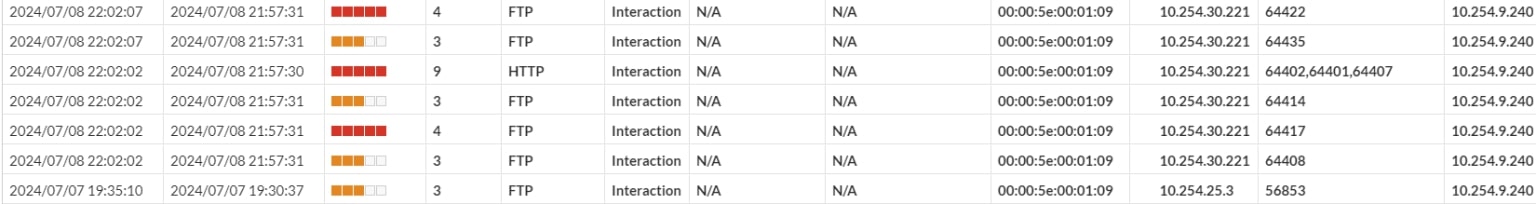
Screenshot 11: Incident list view
After opening the Incident section, you will see a list of all detected incidents.
The list typically includes: the date and time of the incident, the type of attack, the attacker's source IP address, the targeted decoy, and the status of the incident.
Incident Details
By selecting an individual incident, you gain access to a more detailed view.

Screenshot 12: Incident details
Details typically include: a description of the attack, the type of threat (e.g., ransomware, brute-force attack), detailed logs and transcripts of communication between the attacker and the decoy, and potential Indicators of Compromise (IoCs).
Integrating Cyber Deception Systems with Other Defense Technologies
Integrating cyber deception systems with other security technologies is a key strategy in modern approaches to information system protection. Cyber decoys play a crucial role in this integration. They are deliberately designed to attract attackers by simulating vulnerabilities and appealing targets. Through integration with SIEM (Security Information and Event Management) platforms, organizations can centrally collect and analyze attack data. This data serves as the foundation for detecting new threats and optimizing IDS/IPS (Intrusion Detection/Prevention Systems) rules and strategies.
Additionally, decoys integrate with firewall systems to create an extra layer of defense at the network perimeter, preventing attacks before they reach critical systems. Automation through orchestration enables fast and efficient responses to detected threats, minimizing reaction time and reducing potential damage.
This integrated approach allows organizations to proactively identify, analyze, and neutralize cyber threats, significantly enhancing the security and resilience of their network resources in today’s digital environment.
Conclusion
“Know your enemy and you will be victorious.” – Sun Tzu
The quote “Know your enemy and you will be victorious” from Sun Tzu’s *The Art of War* has strong relevance in the context of cyber defense. This principle emphasizes the importance of understanding the characteristics and intentions of attackers to successfully recognize and neutralize cyber threats. By analyzing attack methods, identifying system vulnerabilities, and implementing cyber deception systems such as decoys, organizations can better prepare their defensive strategies and increase their resilience to attacks. Gaining deep insight into threats enables faster response and more effective management of security risks, minimizing potential damage and preserving the integrity of network systems and critical infrastructure. For more information about implementing this solution, feel free to contact us at security@comping.hr.


