The Industrial Revolution of the 18th century marked a turning point in human history. With the introduction of the steam engine, the world entered an era of mass production, efficiency, and technological advancement. But alongside this revolution came new challenges — the safety of machines, workers, and the entire production process became a priority. Today, in the era of the Fourth Industrial Revolution (Industry 4.0), we are witnessing a similar transformation, but with one crucial shift: digitalization has replaced steam, and cybersecurity has become a central everyday concern.
Just as steam engines required safety valves to prevent damage to machinery, today’s industrial networks require adequate system protection.
This blog illustrates how implementing cybersecurity in OT networks can bridge the gap between traditional industrial practices and modern digital threats, creating a secure environment for innovation. By comparing historical developments, we will analyze how the industrial sector is adapting to the challenges of the new era and which key strategies protect critical infrastructure.
What Is OT and How It Differs from IT Networks
Operational Technology (OT) encompasses hardware and software used to control, monitor, and automate physical devices, processes, and systems in industrial, energy, transport, and other critical sectors. This includes Industrial Control Systems (ICS), SCADA systems, DCS (Distributed Control Systems), and PLCs (Programmable Logic Controllers). The primary goal of OT networks is to ensure stable, reliable, and safe operation of physical processes.
In contrast, Information Technology (IT) focuses on data management, communication, and business processes. IT networks are designed to process large volumes of data and provide users with access to information via internet applications or business systems. While IT prioritizes confidentiality, integrity, and availability of data (the CIA triad), OT focuses on the availability and safety of physical systems, with confidentiality playing a much smaller role.
The Convergence of IT and OT: New Challenges in Connected Networks
Operational technologies (OT) that control industrial processes — such as SCADA systems, controllers, and sensors — are increasingly connected to IT networks, the internet, and cloud services. This connectivity provides opportunities for optimization, but also opens the door to new types of threats. Once isolated networks are now exposed systems vulnerable to cyberattacks, with potential consequences such as production outages, financial losses, or threats to human safety.
Historical Context: Stuxnet — The Beginning of the Cyber Threat Era in Industry
In 2010, an event occurred that changed the way we think about cybersecurity in industrial environments. Stuxnet, the first known cyberattack designed specifically to sabotage Industrial Control Systems (ICS), revealed how vulnerable modern operational systems are when targeted.
This sophisticated computer worm targeted Siemens PLCs (Programmable Logic Controllers) that controlled centrifuges at Iran’s Natanz nuclear facility. By exploiting four zero-day vulnerabilities — an unprecedented occurrence at the time — Stuxnet demonstrated how malware could infiltrate isolated OT networks undetected, manipulate their operations, and cause physical equipment destruction. Its precision, targeting, and sophistication marked a new era of threats where cyberattacks were no longer just about stealing data but also causing real-world physical damage.
The historical significance of Stuxnet lies in the fact that it set a precedent for future attacks on critical infrastructure, including energy grids, manufacturing plants, and transportation systems. It exposed weaknesses in OT security standards, which had relied heavily on physical isolation (air gap) as the primary defense mechanism.
Why OT Networks Need Microsegmentation
In the world of Industrial Control Systems (ICS) and Operational Technology (OT), network security plays a key role in protecting critical infrastructure.
This is where network microsegmentation comes in — a strategy that creates logical security zones within the network, preventing unauthorized access and the spread of threats. Just as modern buildings use security doors to control access to different rooms, microsegmentation enables precise control over communication within an OT network.
This method enhances traditional network segmentation, which divides networks into larger zones using VLANs and firewalls. While segmentation ensures basic separation, microsegmentation goes much further — it enforces strict rules within those segments, limiting access even between devices in the same network environment. This means that even if an attacker compromises one device, they cannot freely move laterally across the network.
By applying network microsegmentation in OT systems, organizations can significantly reduce their attack surface and protect critical operations, ensuring the stable and secure functioning of industrial processes.
Network Microsegmentation: ICS Security Through the Lens of Safety Systems from the First Industrial Revolution
Imagine a scenario from the First Industrial Revolution, where factories used complex machinery performing specialized tasks in different departments. To ensure smooth operations and protect people and property, each department had its own safety measures — guards, locked doors, and supervision that monitored every step of the production process.
In the digital world, the security of Industrial Control Systems (ICS) works in a similar way, but with modern technologies. Instead of guards and doors, we have network microsegmentation, which “restricts” and controls traffic between different parts of the network, just as doors and guards separated production zones in early industrial factories.
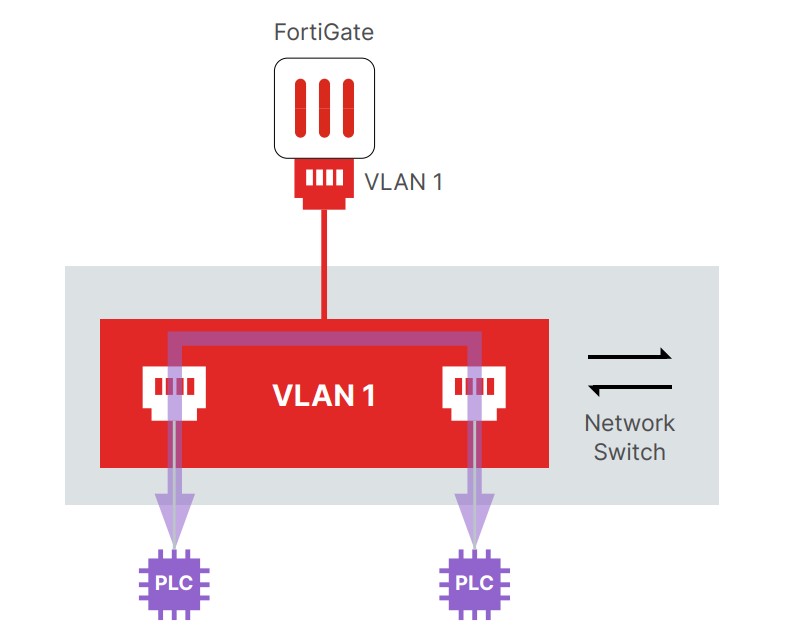
Illustration 1: Traffic flow without microsegmentation
In this comparison, the FortiSwitch switch and FortiGate firewall devices take on the roles of guards and security personnel. FortiSwitch operates at Layer 2, creating “security zones” or VLANs, much like doors that control who can enter specific parts of a factory. The FortiGate firewall, acting like a supervisor, ensures that communication between different zones occurs securely, taking responsibility for routing data across the network. If a device within one zone attempts to communicate with a device in another zone, the FortiGate firewall ensures that such communication is allowed only if explicitly permitted by the security policies.
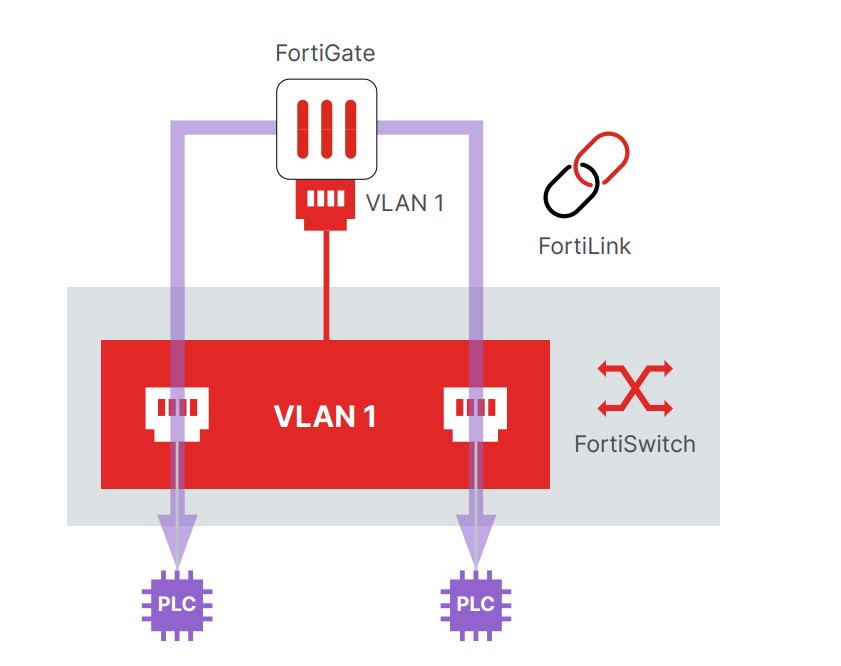
Illustration 2: Traffic flow with microsegmentation
At the highest level, just as detailed supervision and inspections were used in factories in the past, NGIPS (Next-Generation Intrusion Prevention System) on FortiGate devices enables deep inspection of network traffic. This is similar to supervisors during the Industrial Revolution carefully monitoring every production process and taking preventive measures to ensure that all stages of manufacturing operated within safe limits.
This combination of advanced microsegmentation, precise security policies, and proactive monitoring allows ICS/OT network owners to protect their critical systems in much the same way industrial supervisors once protected factory operations — only now with technologies that define modern security and efficiency.
While network microsegmentation provides precise traffic control within industrial networks, the Purdue Enterprise Reference Architecture (PERA) offers a structured framework that enables effective implementation of security policies and optimization of operations across all levels of industrial systems.
PERA Architecture: The Foundation of Modern Industry
The Purdue Enterprise Reference Architecture (PERA) represents a standardized framework for designing and implementing security solutions in Industrial Control Systems (ICS). This approach allows organizations to structure their ICS networks into hierarchical layers, making it easier to apply security policies and controls.
When used in the context of network microsegmentation, PERA provides guidance for the proper placement of security zones and communication channels within an ICS network. This enables granular control of traffic between different parts of the network, reducing the risk of lateral movement and increasing overall system security.
For example, Fortinet’s integrated microsegmentation solution uses PERA guidelines for implementation. By using FortiSwitch switches and FortiGate NGFW devices, this solution extends VLAN capabilities from Layer 2 to Layer 3 (routing) and Layer 7 (application visibility), allowing for deep inspection of network traffic. This integration enables the implementation of security policies based on the zero trust principle, where every device must be verified before communicating with another device, even within the same security zone.
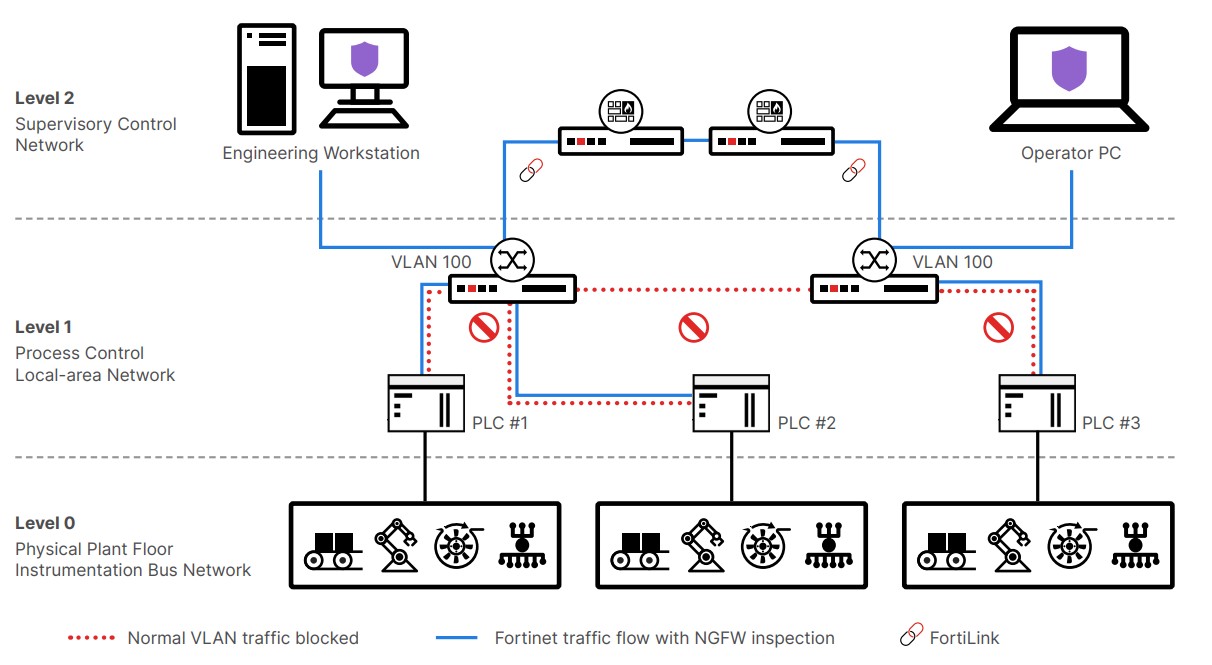
Illustration 3: Example of a PERA-based implementation architecture for network microsegmentation using integrated FortiSwitch and FortiGate devices
From Theory to Practice: Implementing OT Security on the FortiGate Firewall
Implementing security measures in Operational Technology (OT) environments requires precise configuration of network devices to ensure the protection of critical industrial systems. The FortiGate firewall provides powerful tools for segmentation, traffic filtering, and access control, enabling comprehensive security for OT networks. In this section, we walk through key configuration steps and best practices for deploying the FortiGate firewall in an industrial environment, ensuring optimal protection without disrupting operational efficiency.
OT Asset Visibility and Network Topology
Adapting Purdue levels within the FortiGate OT View menu allows for accurate mapping of industrial devices within the network, improving visibility and simplifying the management of security policies. This step lays the foundation for clear system segmentation and defining communication rules between different OT components.
When the Operational Technology (OT) feature is enabled, additional tabs appear in the Asset Identity Center, allowing you to view OT asset lists and OT network topology using Purdue levels. This functionality is available regardless of whether Security Fabric is enabled.
How to Enable OT Features via the GUI:
Go to System > Feature Visibility.
In the Additional Features section, enable Operational Technology (OT).
Click Apply.
After enabling OT features, additional tabs appear under Security Fabric > Asset Identity Center:
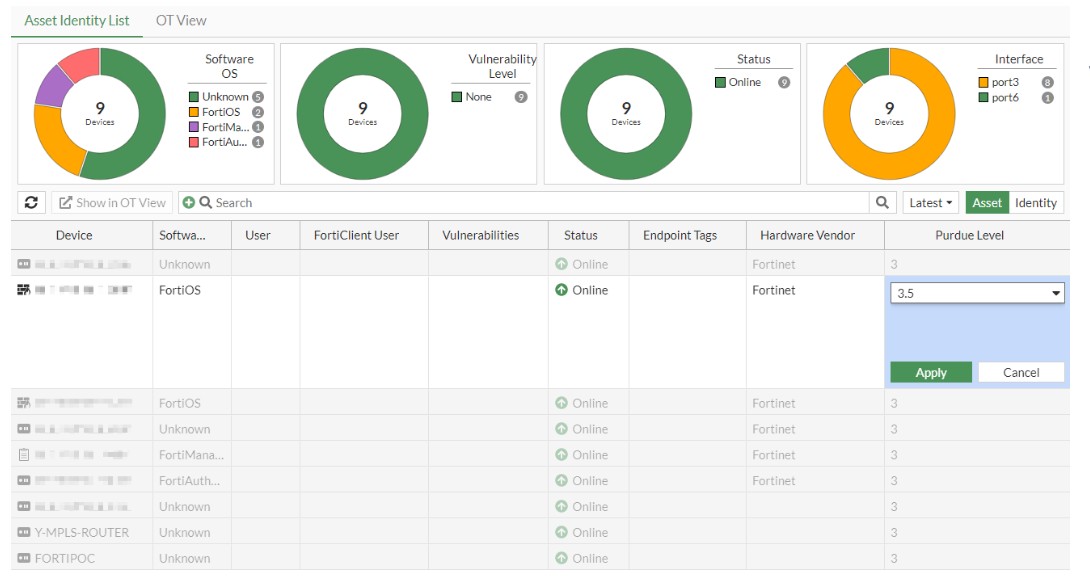
Asset Identity List – displays a list of devices with the ability to assign Purdue levels and view them in the OT topology overview.
OT View – provides visualization of the OT network according to the Purdue model, simplifying the management of security policies and monitoring industrial networks.
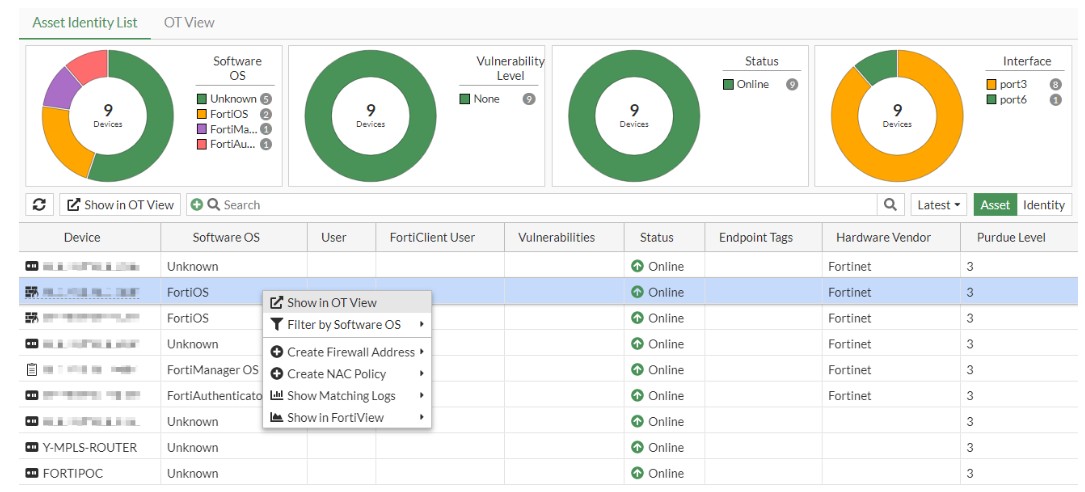
Ilustracija 4: Odabir OT prikaza uređaja
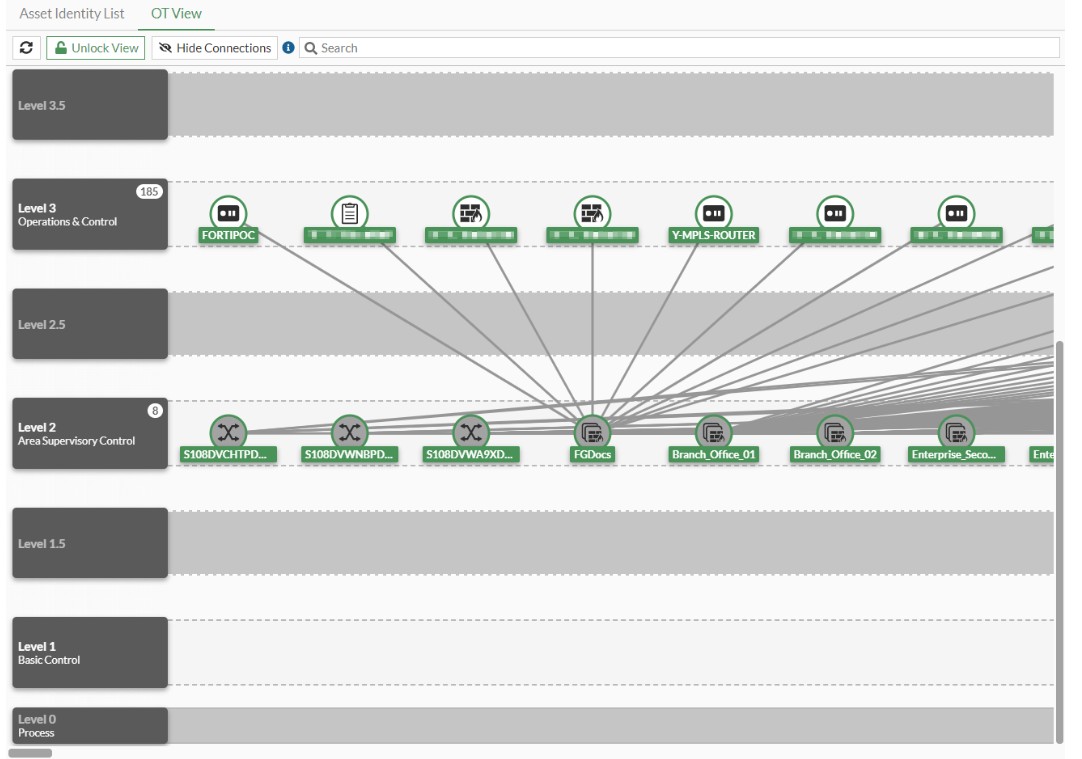
Illustration 5: OT environment view based on the PURDUE model
The FortiGate firewall allows manual adjustment of Purdue levels for identified OT devices within the OT View menu in the Asset Identity Center. This feature provides administrators with a clearer overview of the industrial network and enables more precise segmentation of devices according to the Purdue model, thereby improving security control and overall system visibility.
How to change a device’s Purdue level in the OT View menu:
Open Security Fabric > Asset Identity Center.
Click the OT View tab to visualize the network according to the Purdue model.
Locate the device you want to modify.
Click on the device to open its details.
In the Purdue Level dropdown menu, select the appropriate level (e.g., L0 – Physical devices, L3 – DMZ, L5 – User applications).
Click Save to apply the changes.
Ilustracija 6: Prikaz promjene PURDUE razine uređaja
Također razinu je moguće prilagodit i ”povuci i ispusti” metodom.
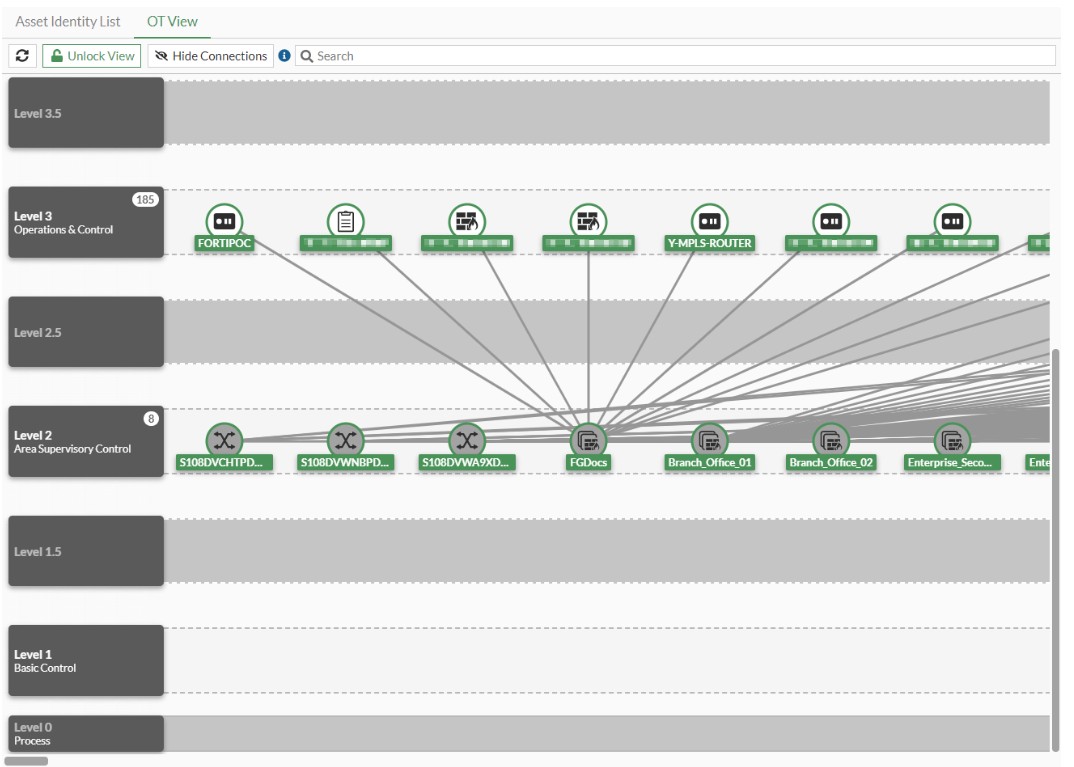
Illustration 7: Changing the PURDUE level using the drag-and-drop method
The next step is creating access control policies on the FortiGate firewall, applying OT IPS (Intrusion Prevention System) signatures. These policies enable traffic control between different Purdue levels, detection of OT-specific threats, and protection of critical industrial systems from potential cyberattacks.
Security Policies in Practice: Access Control and OT IPS Protection on the FortiGate Firewall
Once network segmentation has been implemented at the switch level, each segment of the OT network is now clearly defined according to the Purdue model. However, segmentation alone is not enough to ensure full protection — it is critical to control communication between segments to prevent unauthorized access, limit the spread of potential threats, and maintain uninterrupted operation of critical industrial processes.
In this step, we will implement access control rules on the FortiGate firewall, determining who can communicate with whom and under what conditions. We will also apply OT IPS signatures, enabling deep inspection of OT protocols, detection of threats specific to industrial environments, and blocking of suspicious activity before it can compromise the system.
Steps for Configuring FortiGate Firewall for OT Security
When creating rules on the FortiGate firewall, it is important to apply specialized IPS profiles tailored for industrial protocols such as Modbus, DNP3, or OPC UA. These profiles enable detection and blocking of suspicious activity specific to industrial networks. For example, if an unauthorized attempt is made to send commands to PLC devices, the IPS rule can automatically block that traffic and generate an alert.
It is recommended to combine IPS protection with features such as application control and SSL inspection to ensure deep verification of data passing through the firewall. This ensures that even if an attacker tries to exploit a vulnerability in an industrial protocol within encrypted traffic, FortiGate can detect anomalies and take appropriate action.
Unlocking OT Security: How to Check Your FortiGate License for Industrial Protection
When accessing a FortiGate device to review OT security capabilities, one of the key steps is checking the available licenses. Fortinet provides specialized security services focused on protecting industrial systems, but their availability depends on the active license.
By logging into the administrative interface and navigating to the FortiGuard section, you can view currently active security services. Here you will find information on the status of IPS, Application Control, and specialized protections for industrial protocols. If the OT Security license is active, FortiGate will enable access to advanced IPS databases that include detection and protection against threats targeting SCADA systems, PLCs, and other critical industrial components.
In addition to license activation, it is important to check whether the security databases are up to date. FortiGate regularly downloads new security signatures from the FortiGuard service, ensuring protection against the latest threats. If the license is not active or has expired, industrial security mechanisms may be limited, and the system may be unable to effectively detect potential threats.
This initial check provides a clear picture of how prepared the firewall is to protect the OT environment and enables planning of next steps, whether it involves activating new security features or optimizing existing policies to ensure maximum protection of industrial systems.
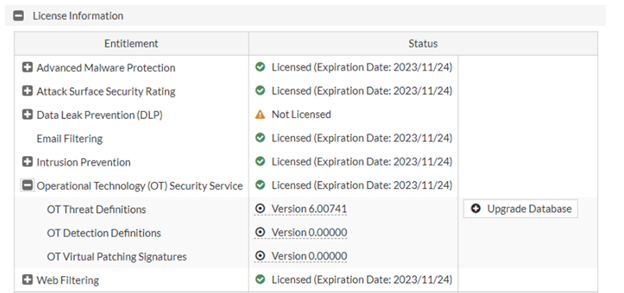
Illustration 7: Changing the PURDUE level using the drag-and-drop method
The next step is creating access control policies on the FortiGate firewall, applying OT IPS (Intrusion Prevention System) signatures. These policies enable traffic control between different Purdue levels, detection of OT-specific threats, and protection of critical industrial systems from potential cyberattacks.
Security Policies in Practice: Access Control and OT IPS Protection on the FortiGate Firewall
Once network segmentation has been implemented at the switch level, each segment of the OT network is now clearly defined according to the Purdue model. However, segmentation alone is not enough to ensure full protection — it is critical to control communication between segments to prevent unauthorized access, limit the spread of potential threats, and maintain uninterrupted operation of critical industrial processes.
In this step, we will implement access control rules on the FortiGate firewall, determining who can communicate with whom and under what conditions. We will also apply OT IPS signatures, enabling deep inspection of OT protocols, detection of threats specific to industrial environments, and blocking of suspicious activity before it can compromise the system.
Steps for Configuring FortiGate Firewall for OT Security
When creating rules on the FortiGate firewall, it is important to apply specialized IPS profiles tailored for industrial protocols such as Modbus, DNP3, or OPC UA. These profiles enable detection and blocking of suspicious activity specific to industrial networks. For example, if an unauthorized attempt is made to send commands to PLC devices, the IPS rule can automatically block that traffic and generate an alert.
It is recommended to combine IPS protection with features such as application control and SSL inspection to ensure deep verification of data passing through the firewall. This ensures that even if an attacker tries to exploit a vulnerability in an industrial protocol within encrypted traffic, FortiGate can detect anomalies and take appropriate action.
Unlocking OT Security: How to Check Your FortiGate License for Industrial Protection
When accessing a FortiGate device to review OT security capabilities, one of the key steps is checking the available licenses. Fortinet provides specialized security services focused on protecting industrial systems, but their availability depends on the active license.
By logging into the administrative interface and navigating to the FortiGuard section, you can view currently active security services. Here you will find information on the status of IPS, Application Control, and specialized protections for industrial protocols. If the OT Security license is active, FortiGate will enable access to advanced IPS databases that include detection and protection against threats targeting SCADA systems, PLCs, and other critical industrial components.
In addition to license activation, it is important to check whether the security databases are up to date. FortiGate regularly downloads new security signatures from the FortiGuard service, ensuring protection against the latest threats. If the license is not active or has expired, industrial security mechanisms may be limited, and the system may be unable to effectively detect potential threats.
This initial check provides a clear picture of how prepared the firewall is to protect the OT environment and enables planning of next steps, whether it involves activating new security features or optimizing existing policies to ensure maximum protection of industrial systems.

Illustration 9: Example of OT application signatures
Security Policies on the FortiGate Firewall
Creating security rules on a Fortinet firewall for OT networks follows the same process as defining rules for traditional IT traffic. In both cases, configuring access control policies involves defining the source and destination addresses, services/applications, and the action (allow or block). The key difference lies in the type of inspection used to identify and control network traffic.
For conventional IT traffic, policies are typically based on ports and protocols such as HTTP, HTTPS, SSH, or SMTP, with security enhanced through IPS, which detects and blocks attacks based on known IT threat signatures. In OT environments, instead of traditional IT protocols, traffic flows through industrial standards such as Modbus, DNP3, BACnet, OPC UA, and IEC 104, which often lack built-in security mechanisms. Therefore, when creating access control rules for OT, specialized OT IPS is used. It relies on application signatures to recognize and filter OT traffic, enabling precise control over communication between industrial devices.
At a practical level, creating rules for IT and OT networks on FortiGate devices looks similar — the administrator defines the source and destination zones, devices, services, and additional security controls such as IPS and application inspection. The difference is that OT access rules use specialized IPS profiles optimized for industrial protocols, ensuring detection of advanced threats specific to critical systems. FortiGate allows fine-tuning of security settings based on IT or OT requirements, ensuring optimal protection for both environments.
Conclusion: From the Steam Engine to the Digital Shield – A New Era of Industrial Security
Just as the steam engine once powered the industrial revolution, today intelligent networks and cybersecurity form the foundation of modern industry. Yet with progress come new challenges — industrial systems, once isolated and safely contained within factory walls, are now connected to the digital world and exposed to threats unheard of in the age of steel and steam.
In this context, FortiGate firewalls become the digital shields of industrial networks, providing precise control over OT traffic, protection against cyber threats, and ensuring the stability of operational systems. Through the use of application signatures, OT-specific IPS, and microsegmentation, industrial facilities can operate safely and efficiently, without compromising between protection and operational performance.
Today, industrial security is no longer just about physical protection of machinery — it has become a strategic necessity, where strength is measured not in horsepower, but in resilience against invisible digital threats. In the era of Industry 4.0, true progress lies in the ability to secure a connected world without sacrificing innovation — and Comping’s expertise in securing OT technologies makes that possible.
For more information about implementing this solution, feel free to contact us at security@comping.hr.



